Empowering Your IT Infrastructure: Essential Technologies for Management and Security
Discover the essential technologies that can help manage ...
10 Signs Your Wi-Fi Network Needs an Upgrade (Part 2)
This article is a continuation of “10 Signs You Need to ...
10 Signs Your Wi-Fi Network Needs an Upgrade (Part 1)
Your WIFI network is one of the most critical components of ...
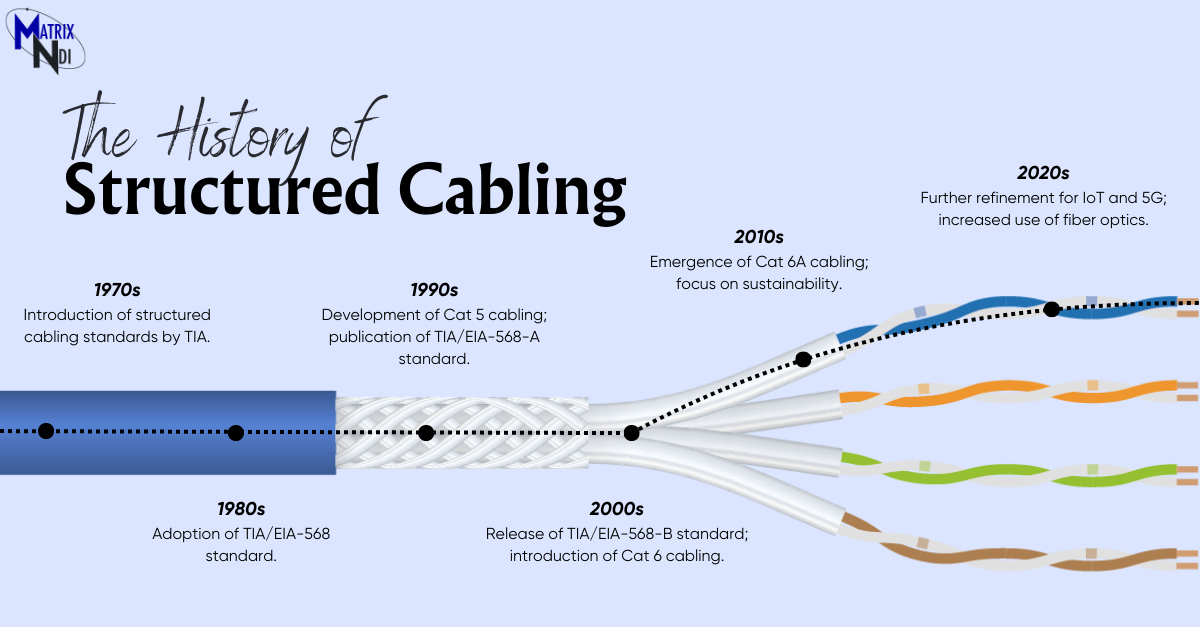
The Evolution of Structured Cabling: A Historical Perspective
Explore the fascinating journey of structured cabling and ...
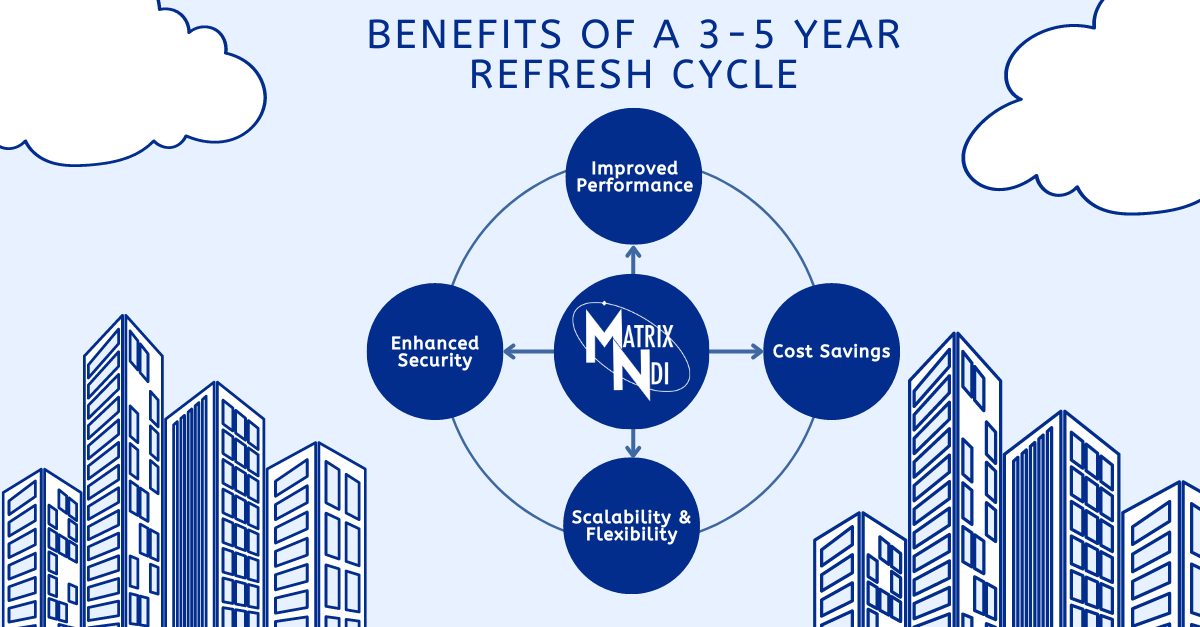
Maximizing Efficiency: The 3-5 Year IT Infrastructure Refresh Cycle
Discover the benefits of implementing a strategic IT ...
10 Things IT Infrastructure Controls for Your Business
In this blog post, we'll explore 10 key aspects that IT ...
The Essential Guide to IT Infrastructure Planning
Discover the key steps and considerations for effective IT ...
Understanding the Basics of a Structured Cabling System
Discover the fundamentals of a structured cabling system ...
Why Choose Matrix-NDI for Your Next IT Project?
Discover the advantages of choosing Matrix-NDI for your ...
Ringcentral Transition Tips: Ensuring a Successful Migration
Discover valuable tips to ensure a smooth and successful ...
Unveiling WiFi 7: A Leap Forward in Connectivity
Staying connected is at the forefront of our daily lives. ...
The Increasing Significance of IT Infrastructure in Business
In today's digital age, IT infrastructure plays a crucial ...
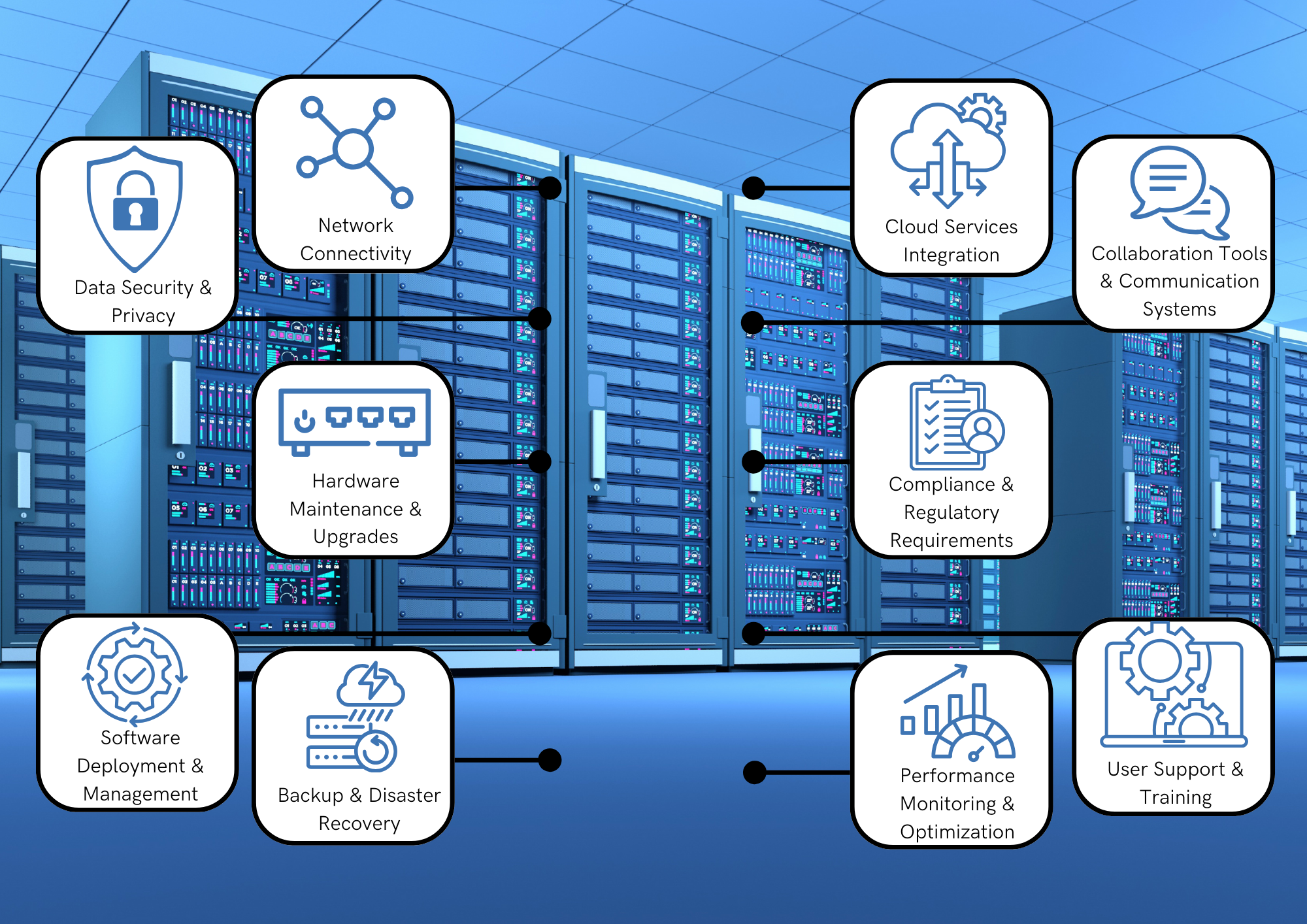
What is IT Infrastructure? - The Backbone of Technology
IT Infrastructure's main components generally consist of an ...
Structured Cabling: Everything You Need to Know
If you're running a business, it's important to make sure ...
The Importance of Cleaning Your Data Center
For almost every company, regardless of size or industry, ...
IT Security Management: What You Need to Know
Taking steps to limit cyber-attack risk. IT security is an ...
Demystifying IT Infrastructure for Beginners
Introduction Information technology (IT) is the foundation ...
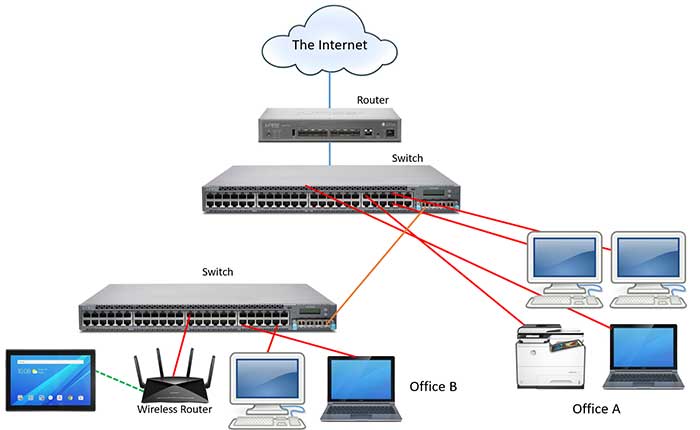
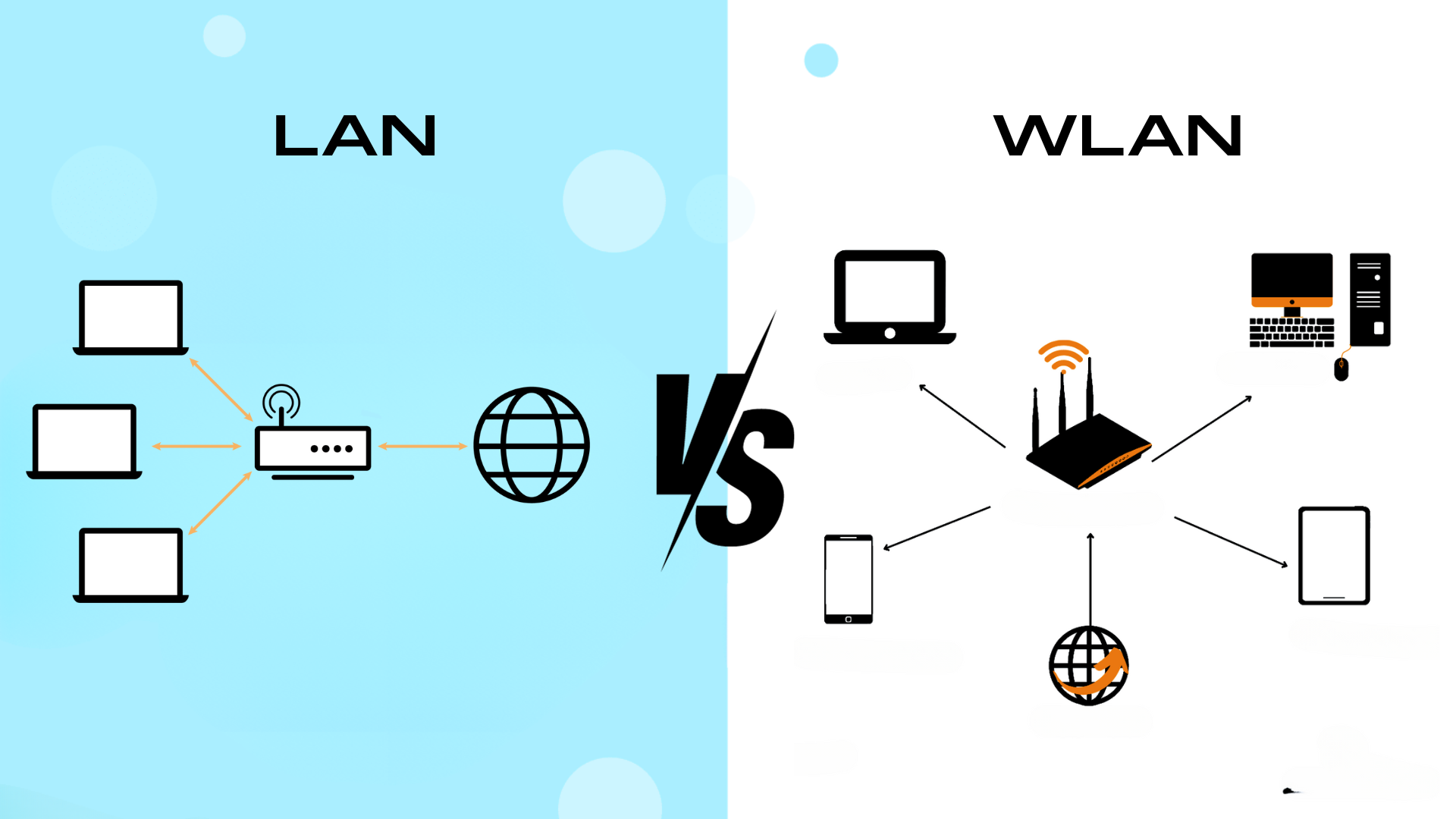
LAN vs. WLAN: Bridging the Wired and Wireless Worlds
Introduction Local Area Networks (LANs) and Wireless Local ...
The Backbone of Connectivity: The Crucial Role of Structured Cabling
Introduction At the core of today's communication systems, ...
10 Helpful Hints When Choosing a UcaaS Solution
As organizations traverse the digital realm, the quest for ...
9 Reasons You Should Use Cat6 Over Cat5e Cabling
Cat6 (Category 6) and Cat5e (Category 5e) are both types of ...
5 Key Signs It's Time to Refresh Your IT Infrastructure
Businesses rely on robust IT infrastructure to stay ...
Unifying Business Communication: The Power of UCaaS
Seamless communication and collaboration are essential for ...
What are the cybersecurity risks with video surveillance?
Cybersecurity is a concern for businesses in every sector, ...
Structured Cabling - More Than Just Pretty Cables
Is an investment in Structured Cabling right for your ...
Scalability and Wi-Fi: Scaling Your Business Network Without Compromising Performance
In the contemporary business landscape, where technology is ...
The Impact of Data Cabling on Network Speed and Stability
A fast and reliable network is crucial for both businesses ...
SD-WAN: Your Guide to the Future of Networking
In the fast-paced digital landscape of today's business ...
Understanding PoE (Power over Ethernet) and Its Applications
In the realm of networking and technology, innovation ...
Wireless vs. Wired Networks: Debunking the Data Cabling vs. Wi-Fi Myth
The debate between wireless and wired networks has been ...
Wireless Network Design: Key Considerations for Performance
In today's hyper-connected world, wireless networks have ...
Five Benefits of Upgrading to a Business Fiber Network
Upgrading to a business fiber network is an excellent ...
Top 5 Things to Consider When Buying a Business Access Control System
Business access control systems are a common feature ...
Wireless Network Troubleshooting: 10 Common Problems (part 2)
Minimizing downtime and creating a stable wireless network ...
Why a Heat Map is Important For a Wireless Site Survey
A WiFi heat map is a method of testing the strength of your ...
Wireless Network Troubleshooting: 10 Common Problems (pt 1)
Wireless networks are critical for the smooth operation of ...
Matrix-NDI Telecom 10 Podcast 7: Wi-Fi Basics
In this episode of our Telecom 10 podcast, we’re speaking ...
Cat5 vs. Cat6 Cable - Which is Right for You?
As an end user you probably don’t put a ton of thought into ...
Matrix-NDI Telecom 10 Podcast 6: SASE Post-COVID
In this episode of our Telecom 10 podcast, we’re speaking ...
Your Simple Guide to Wireless Networks
Wireless networks are crucial for mobility and flexibility ...
How Fiber Optic Cables Work: An Explanation for Non-Engineers
Do you ever stop to think about how all of the technology ...
What is CryptoLocker? It is a type of Malware.
CryptoLocker is a type of malware that is damaging for ...
Matrix-NDI Telecom 10 Podcast 4: UCaaS
In this episode of our Telecom 10 podcast, we’re speaking ...
Matrix-NDI Telecom 10 Podcast 3: E-rate Funding for K-12
In this episode of our Telecom 10 podcast, we’re speaking ...
Matrix-NDI Telecom 10 Podcast 2: Interview with Jason Cardwell
In this episode of our Telecom 10 podcast, we speak with ...
Matrix-NDI Telecom 10 Podcast 1: Interview with Frank Millo
In this, our very first Telecom 10 podcast, we speak with ...
How to Choose a Cloud-Based Video Surveillance System
Choosing a new cloud-based video surveillance system can be ...
Why Your Structured Cabling Network is Critical for IT Security Management
The structured cabling network is a topic that many ...
The Beginner's Guide: Facial Recognition
Facial Recognition has been a huge buzzword for a couple of ...
Top 5 Things That Have Changed as a Technology Company in Minnesota
As a technology company in Minnesota, we have seen some ...
Why National IT Deployments Require Professional Project Management
When our customers come to us with a new IT infrastructure ...
7 Ways to prevent a ransomware attack - Part 2
Entrprise IT Planning Can Stop Ransomware Now that you have ...
7 Ways to prevent a ransomware attack - Part 1
Ransomware at its core is a data hostage situation For ...
The Benefit of Working with Matrix-NDI for UCaaS
It’s no secret that the world is moving from premise-based ...
Why Disaster Recovery Planning is Important
Disaster recovery planning is crucial to safe business ...
Returning to the Office: Assessing Your IT Infrastructure
As we begin to see the light at the end of the tunnel ...
Wired vs. Wireless LAN: Which is best for your business? (Part 2 of 2)
Part 2: Diving Deeper on Wired and Wireless LANs In Part 1 ...
Wired vs. Wireless LAN: Which is best for your business? (Part 1 of 2)
Wired vs. Wireless LANs The debate of wired vs. wireless ...
Your IT Security and Access Control Checklist
Protecting your sensitive data Do you know what to do when ...
Cybersecurity: Mixing Personal and Corporate Cloud Accounts
Businesses all over the globe have moved to a remote work ...
Using the Cloud Still Requires IT Infrastructure
Cloud Solutions. Cloud Technology. Cloud Servers. ...
Top 5 Reasons to Implement Cloud Video Surveillance - VSaaS
Video Surveillance as a Service (VSaaS) is a hosted, ...
6 items to consider on Disaster Recovery (DRaaS)
Disaster Recovery as a Service (DRaaS) Millions of ...
How the Microchip Shortage Impacts Premise-Based Phone Systems
We have all heard about the microchip shortage over the ...
Wired vs. Wireless Network: Which is Better?
To be Wired or Wireless? That is the question when it comes ...
Case Study: Making the Change to RingCentral
Communication is the backbone of business today and making ...
The Importance of IT Infrastructure Health Checks
Technology is an ever-evolving field. The hardest part is ...
How Certified Structured IT Cabling Technicians Can Benefit You
Structured IT Cabling Technicians are professionals in the ...
How to Plan Your IT Infrastructure Transformation
Planning or mapping out your IT infrastructure can be a ...
How Structured IT Cabling is Important in the Age of Cloud Solutions
A common misconception is that cloud solutions and cloud ...
10 Questions You Should Ask Potential Security Solutions Providers
The term security covers everything from physical building ...
10 Questions You Should Ask Potential Voice Applications Providers
Unified Communications as a Service (UCaaS) is a key ...
10 Questions You Should Ask Potential Low Voltage Cabling Providers
Infrastructure is a component of a business that is rarely ...
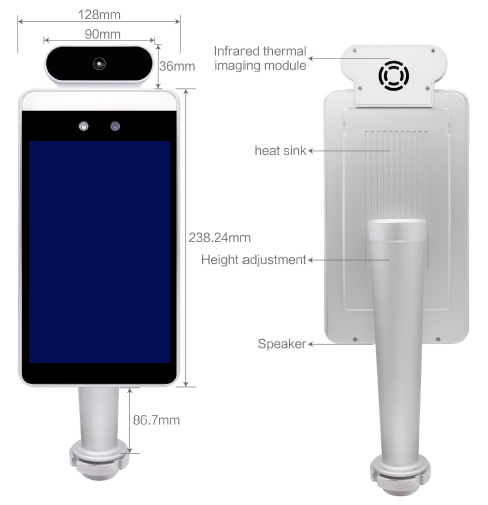
Temperature Scanner Kiosk with Facial Recognition
As we are all aware, COVID-19 has changed the way ...
Emergency Services Information - Dialing 911 with a Corporate Softphone
Important Emergency Information Regarding IP Telephones and ...
Temporary Technology Solutions Create Permanent Problems
In many aspects of our lives we make decisions every day. ...
Retirement Announcement - Steve Cosgrove
After almost 17 years with Matrix-NDI working as a Field ...
Contact Center as a Service (aka CCaaS)
What is a contact center? Simply put, a contact center is ...
UCaaS - The Breakdown of Cloud Communication
Communication is a simple concept, right? You have a phone, ...
Building Automation Systems (BAS) and Intelligent Buildings
What is a Building Automation System (BAS) ? Building ...
3 Needs to Consider with Healthcare Cloud Communication Platforms
Patients of any hospital, clinic, or specialty center are ...